How to find Exploits and Vulnerabilities in Joomla

After the latest code injection alert [CVE-2015-8562], we decided we all needed some help diagnosing and removing infections, and started implementing it in Little Helper.
LittleHelper (version 2.4.2) features a new function in its Security view: "Search for Exploits".
Please consider this is just a utility to help you diagnose potential issues; you still need to patch your Joomla version, test it against a backup taken before Dec. 10th, 2015, and run proper antimalware.
While extremely simple in its approach, it does help system administrators and webmasters identify potential issues with their installations.
A window pops up, and - in what could be a long time - starts showing information:
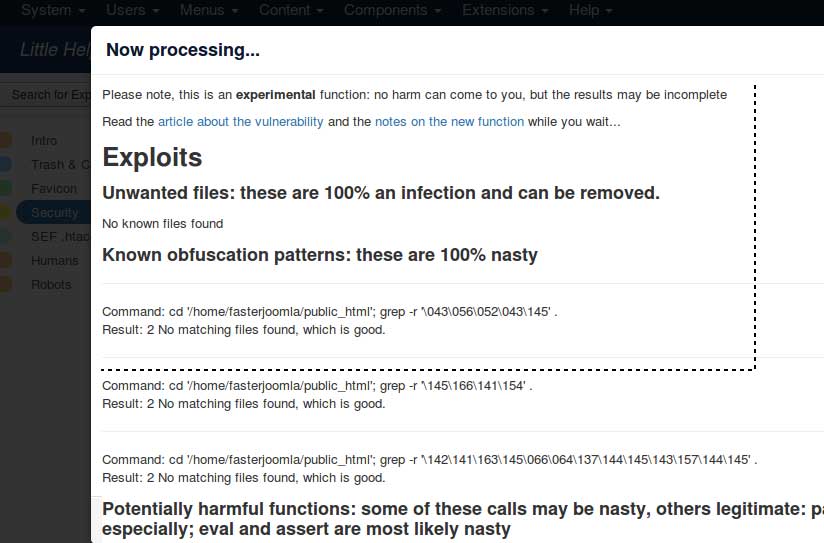
Please bear with the redundancy, this is meant just as an extra means of identifying nasty stuff.
But it will catch plenty of good code too, so read carefully; hover over the "info" and "code" tags at the beginning of the errors to learn more
Short FAQ for versions 2.4.x
My antivirus complains
Yes, we know. Both the cache deletion and the jedchecker libraries contain calls that can be mistaken for viruses. At first, with just the cache calls, it was just one false positive per year, and it was something we could handle. But then with the jedchecker it simply became overwhelming. The feature is still available with version 2.5.9 and is not installed starting from version 2.6.1. If you are updating a previous installation, and want to remove it manually, simply delete the two folders:
There is also a plan to make the cache cleaning more antivirus-friendly.
I get a timeout error
Your webserver configuration does not allow overriding the default timeout; this script currently takes 1 to 10 minutes to run, so it may very well exceed the default php timeout. Either you change the configuration of the server, or you wait for the next and improved version*.
I get the error 'grep command not found'
This script relies on the gnu grep utility; if you're running on windows, or on limited hosting, this may not be available. Wait for the next and improved version*.
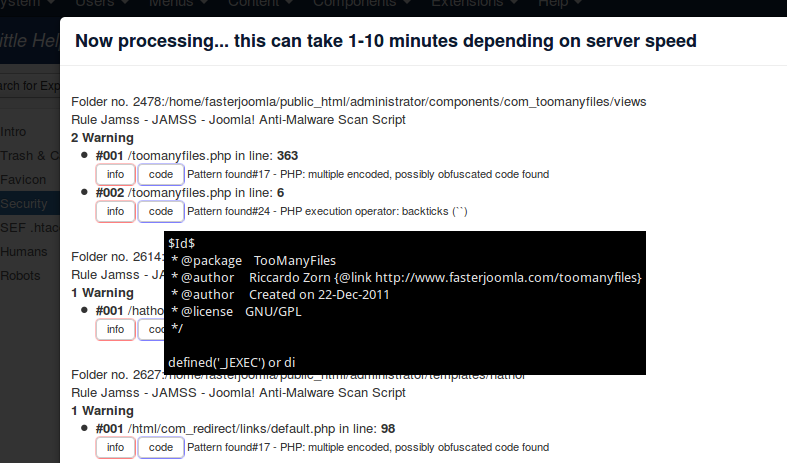
This function dumps hundreds of lines
Alas, identifying malware is for human eyes; we can only attempt to spot patterns that could be used maliciously; but they can be used legitimately as well! Hover over the "info" and "code" elements in the JAMSS section of the results to see the relevant code.
I clicked and the report disappeared, do I have to run it again?
Alas, yes. Wait for the next and improved version*.
What's with the "next and improved version"
We are perfectly aware this function leaves a lot to be desired in compatibiliy, usability, speed, effectiveness; nonetheless, we have at times found it useful and we thought we'd share it. There are currently no plans for building a proper and more effective interface, as this will be addressed by TooManyFiles pro.